Implementing Best Practices to Prevent Breaches
Cyber threats are ongoing and constantly evolving, placing a company’s financial and human resources, intellectual property, facilities, and data at risk. Even intangibles such as your company’s reputation and credibility can suffer irreparable harm. Ideally, cybersecurity should be integrated into a company’s operational and strategic planning process, involving input from all functions and organizational levels. In this way, you will be prepared for the inevitable challenge to your system preparedness.
In-Source Cyber Protection is a comprehensive and agile platform, developed by our cybersecurity team recognized for its cybercrime detection and prevention experience. We enhance your existing cybersecurity resources and bulletproof systems with an infrastructure you control and manage in-house. IoTech Protect supports development and execution of these long-range strategic plans, helping you adapt to the ever-changing threat landscape.
Today, cybersecurity is an integral part of a company’s business life as a necessary asset
- An organization’s cyber security strategy must include the entire organization.
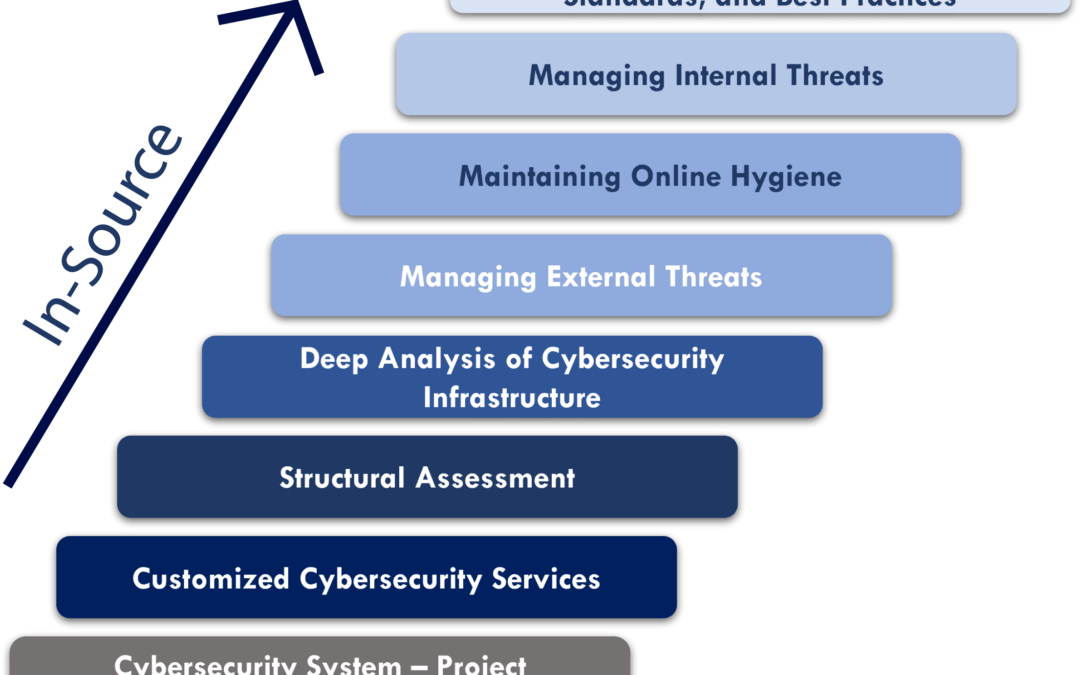
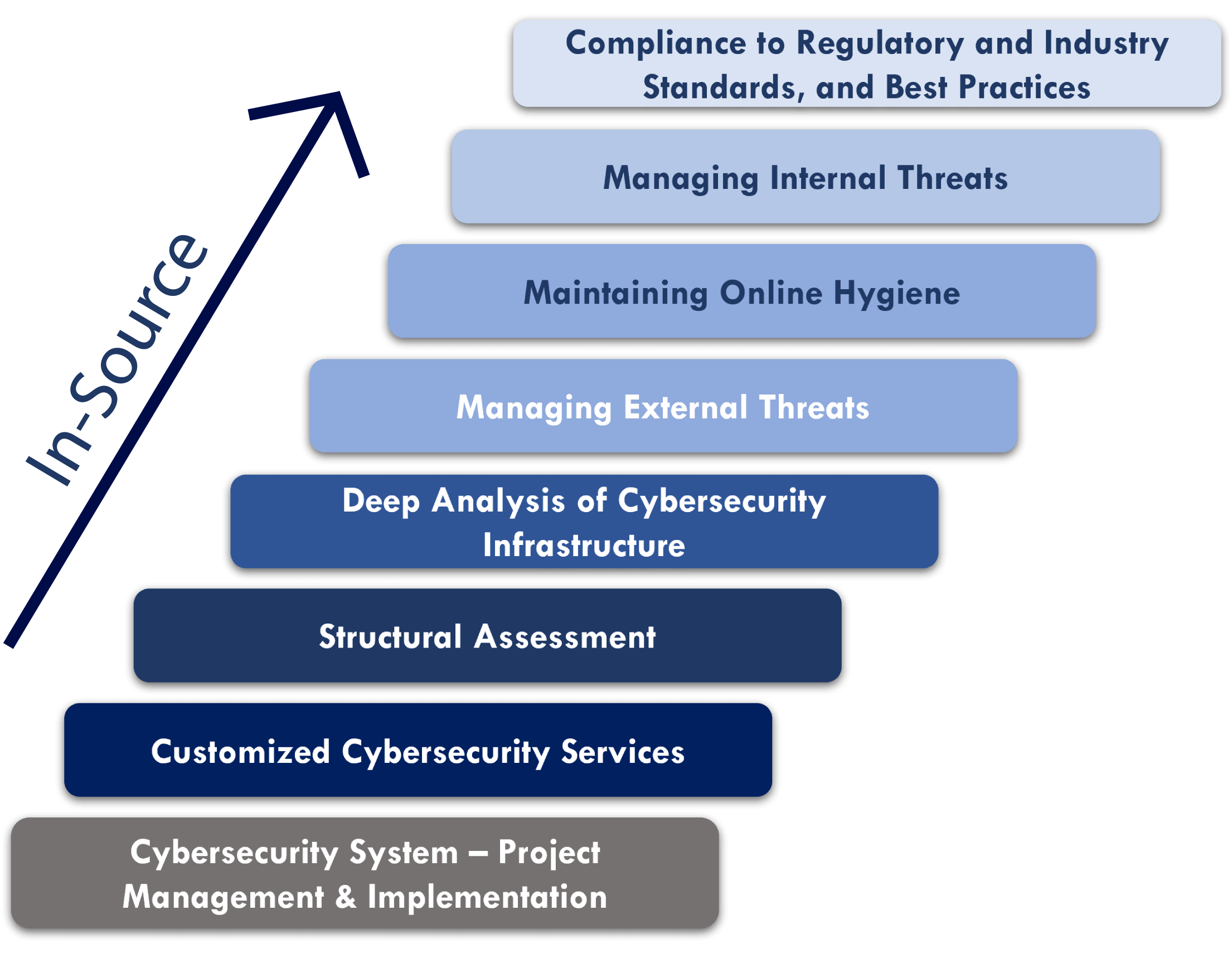
- ‘In-Source’ provides guidance & support to companies towards building the highest level of its own cybersecurity team and infrastructure, aligned with their specific industry standards and best practices, including:
- Helping strengthen their internal team to ensure operational efficiency of their digital security infrastructure.
- Never accessing their proprietary data.
- Helping ensure ongoing understanding of constantly changing/evolving cybersecurity threats.
IoTech Protect’s In-Source solution helps decision-makers, managers, and IT staff develop their organization with organized mapping of cybersecurity requirements in sync with its long-term business growth, at least over a 3-5 year period.
To learn more about the fundamentals of cyber security, read IoTech Protect’s cybersecurity services page.
Our cyber security team stands ready to help meet your needs, with:
- Integrating IoT devices with third-party and in-house applications
- Compliance with regulatory and industry standards and best
- Managing internal and external threats
- Maintaining online hygiene
- Performing analysis of cybersecurity infrastructure
- Structural assessments
- Customized cybersecurity services
- Project management and implementation
Contact Us to learn how we can help mitigate risk and protect your online presence.