Cyber Security


Cyber Security


IoTech Protect Optimized Cyber Protection
IoTech Protect works with organizations’ teams to develop internal infrastructure and processes to assess cyber security threats and challenges. IoTech Protect detects and prioritizes system vulnerabilities and implements best practices to prevent breaches – now and in the years to come.
Cyber Security
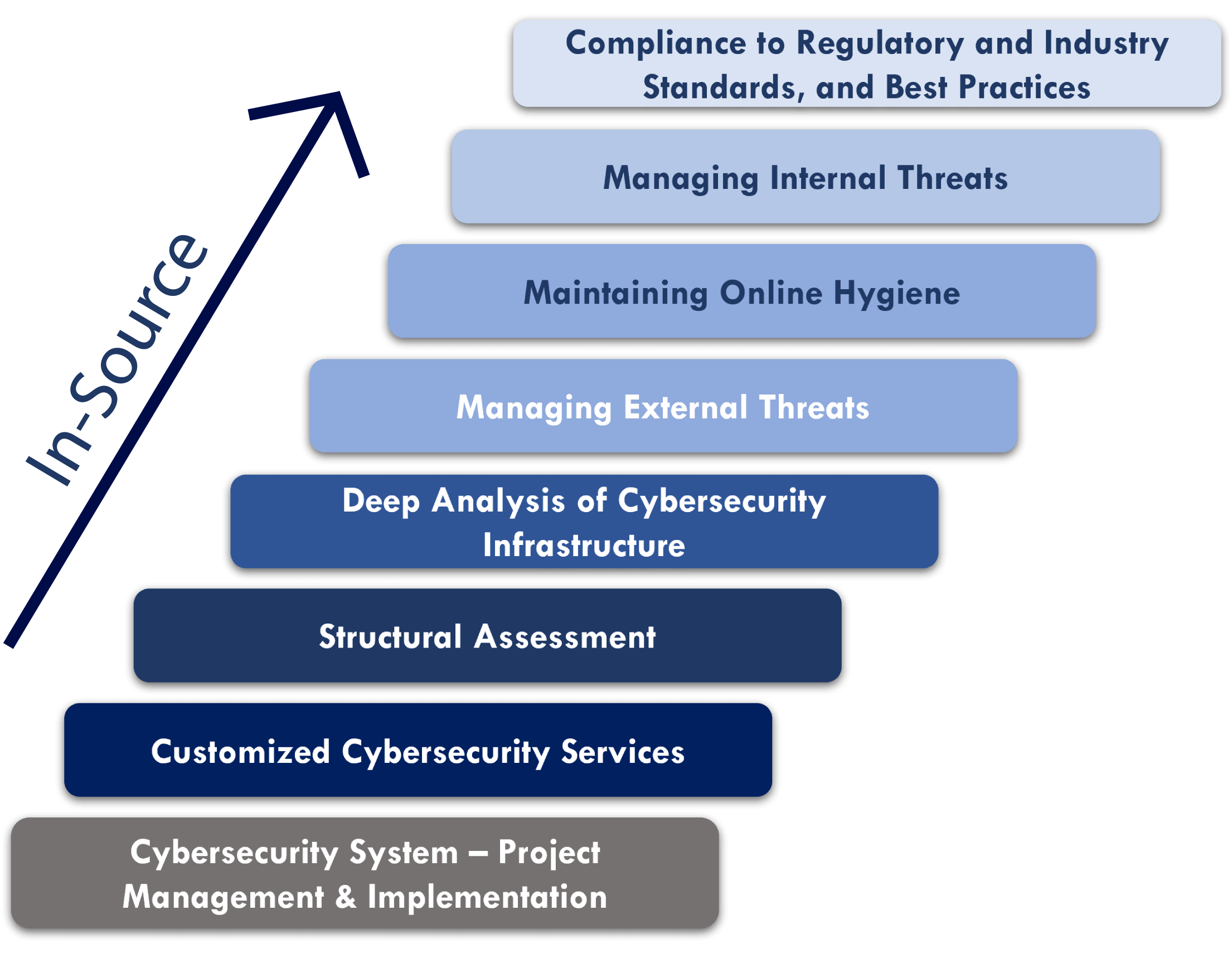
In-Source Cyber Protection
In-Source Cyber Protection is a comprehensive and agile platform, developed by our cybersecurity team recognized for its cybercrime detection and prevention experience. We enhance your existing cybersecurity resources and bulletproof systems with an infrastructure you control and manage in-house. IoTech Protect will support the development and execution of these long-range strategic plans, helping you adapt to the ever-changing threat landscape.
IoTech Protect
Public Key Infrastructure (PKI)

Protecting data and authorizing remote and on-premise equipment and users is essential to keeping your business secure. In collaboration with PrimeKey/KEY FACTOR, IO Tech Protect builds, manages, and helps clients maintain a best practice, proven, and compliant PKI system.
IoTech Protect
Components of PKI

EJBCA Enterprise
A powerful and flexible way to issue, manage, and maintain digital certificates. This is a complete PKI management system built on an open-source platform. It secures data, user identities and physical devices with encryption and managing, authorizing, and securing certificates for system use.

SignServer
A versatile server-side application for creating digital signatures. Digital signature software, with Time Stamping, based on PKI signing used to sign any digital document, code, PDFs, ePassports, and more. SignServer is used as an embedded part of many widely known signing systems.
Identity Authority Manager
Enables users to securely issue digital certificates or ‘birth certificates’, for devices and units during the production process, so the data exchange is securely authorized and protected from unauthorized usage.

PrimeKey SEE
First patented and protected full-size, rack-mounted Intel x86 server for critical data and hardware protection from operating system to virtualization to application.
IoTech Protect
Cyber Laboratory: Security Simulation
- Cyber Laboratory is a physical venue designed to simulate infrastructures to identify hardware and software-based open nodes and other potential internal and external vulnerabilities.
- Developed by a highly-skilled team of professionals with direct, hands-on, expertise in cyber-crime units for forensic analysis of system vulnerabilities and complete physical infrastructure.
- Cyber Laboratory can be used by private and public organizations, as well as in academic settings to allow learning and practice finding system vulnerabilities.
- Cyber Laboratory allows clients to learn the latest innovations, troubleshoot response methodology, and test resistance to specific cyber threats. The goal is to reduce security risks and ensure compliance with the security and specific industrial regulations, protocols, and best practices.
- A Cyber Laboratory can be set up at your location or at one of our regional sites to best meet customer needs.
IoTech Protect Team
Global Experience
- Cybersecurity for financial, health and pharmaceutical sectors.
- Cybersecurity for software development companies.
- Digital forensic analysis in international environments.
- Cyber intelligence: Cyber-crime units within law enforcement, military, & the private sector.
- Each member with more than 11 years experience in cybersecurity.
- Securing critical national infrastructure for countries in Eastern Europe.
- Recognized for work with Law Enforcement Agencies worldwide, including the FBI Director’s Award, BKA Germany, Serbian police Ministry.
- Recognized for contribution to international cyber operations teams including BKA Germany, Serbian police Minister.
- Extensive identification, analysis and takeover of malware infrastructure.
- Global threat hunting for private sector clients.
Get Started
Learn how to protect your business with IoTech Protect
