News & Resources
News & Press Releases
- IoTech Protect Announces Strategic Partnership with Viisights for AI-driven video analytics
- Viisights partners with IoTech Protect on AI video analytics
- Survey reveals cyber, quality challenges of vehicle connectivity
- White House Proposes $10.9 Billion Budget for Cybersecurity | SecurityWeek.Com
- Smart City Internet of Things Innovation (SCITI) Labs
- Automotive IQ: publishes news, articles and more about the connected, autonomous, shared and electric future of the car and aircraft industry.
- Cybersecurity Today Podcast
- What threat does ransomware present in the United States?
- U.S. Gov Issues Stark Warning, Calling Firmware Security a ‘Single Point of Failure’ | SecurityWeek.Com
Internet of Things
Device & Manufacturing Connectivity (OT)
OverviewOT (operational technology), is the practice of interdependent hardware and software to control industrial equipment. OT devices and software primarily interact with the physical world. OT includes industrial control systems (ICSs) like programmable logic...
What is IoT?
The foundation of IoTech Protect’s Digital Asset Protection Service is to provide integrated security solutions that protect a company’s digital, physical and interpersonal spaces in the 21st century, saving costs and resources in the process. Every internet-connected...
Cyber Security
How to Mitigate Cybersecurity-Related Risk
How to Mitigate Cybersecurity-Related RiskIn the Internet age, data is an increasingly valuable asset; data on all aspects of modern life is captured, stored, and processed online. Some say Data is like the new oil. Data warehousing and machine learning techniques...
What is a Cyber Laboratory?
What is a Cyber Security Laboratory?Cybersecurity professionals are responsible for protecting IT infrastructure, edge devices, networks, and data. More granularly, they are responsible for preventing data breaches, monitoring, and reacting to cyber attacks. The best...
What is PKI?
What is PKI?PKI (or Public Key Infrastructure) is the framework of encryption and cybersecurity that protects communications between the server (your website) and the client (your users). Think about all the information, people, and services that your team...
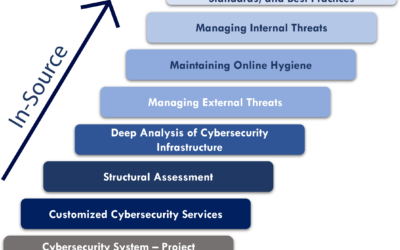
What is In-Source Cyber Protection?
Implementing Best Practices to Prevent BreachesCyber threats are ongoing and constantly evolving, placing a company’s financial and human resources, intellectual property, facilities, and data at risk. Even intangibles such as your company's reputation and credibility...
What is Cyber Security?
What is Cyber Security?Cyber security is the application of technologies, processes, and controls to protect systems, networks, programs, devices, and data (IoT) from cyber attacks. Effective cyber security involves building awareness throughout the entire enterprise...
Physical Security
Biometric Recognition
What is Biometric Recognition?Biometric recognition is an automated information system that allows the identification of a person or group of people based on physiological and behavioral characteristics.Biometric Recognition: How it WorksCompanies can implement...
What is Advanced Physical Security?
Physical and perimeter security traditionally involves a combination of internal and external physical barriers, cameras monitored by security personnel, and device scanning such as card-readers. These methods are expensive, require large numbers of staff to observe...
Get Started
Learn how to protect your business with IoTech Protect